CBDC: Lösung der Regierung für die Rettung eines korrupten Banksystem oder sicheres Rezept für eine Katastrophe?

CDBCs sind auf dem Weg — jetzt spricht die Politik in den US es laut aus.
CBDCs kommen
und mein Eindruck, was das für unser Geld bedeutet, teile ich gerne:
In den letzten 12 Monaten sind 850 Milliarden Dollar an Einlagen von den Banken abgezogen worden. Aber das war nur der Anfang. Allein in den letzten drei Wochen wurden 130 Mrd. USD abgezogen. Wir sind Zeugen eines nationalen Bank-Runs in den USA, der in Zeitlupe abläuft. Was ist die Ursache dafür? Die Menschen wollen ihre Einlagen nicht bei einer Bank halten, die 0,01 % zahlt, wenn Geldmarktfonds über 4 % zahlen.
Mit anderen Worten: Die Regierung/Zentralbank im Auftrag der Regierung konkurriert mit ihrem eigenen Bankensystem um Gelder, und die einzige Möglichkeit, den Bank-Run zu stoppen, ist Senkung der Zinsen. Aber natürlich hat man Angst, dass eine Zinssenkung die Inflation weiter anheizen könnte – der stark geschönte Verbraucherpreisindex in den USA lag im Februar bei 6 %. Das ist eine Zwickmühle, und die Folgen sind schrecklich. Diese Politik hat bereits das schlimmste Gemetzel an Bankzusammenbrüchen seit 2008 verursacht.
Die Credit Suisse – ein 167 Jahre altes Institut – ist über Nacht verschwunden. Vermutlich wäre die Fed von all dem etwas überfordert gewesen. Aber nein, inmitten dieses Blutbads fand sie irgendwie die Zeit, die Einführung eines aufregenden neuen Dienstes namens FedNow im Juli anzukündigen. FedNow ist eine digitale Zahlungsinfrastruktur, die von der Fed kontrolliert wird.
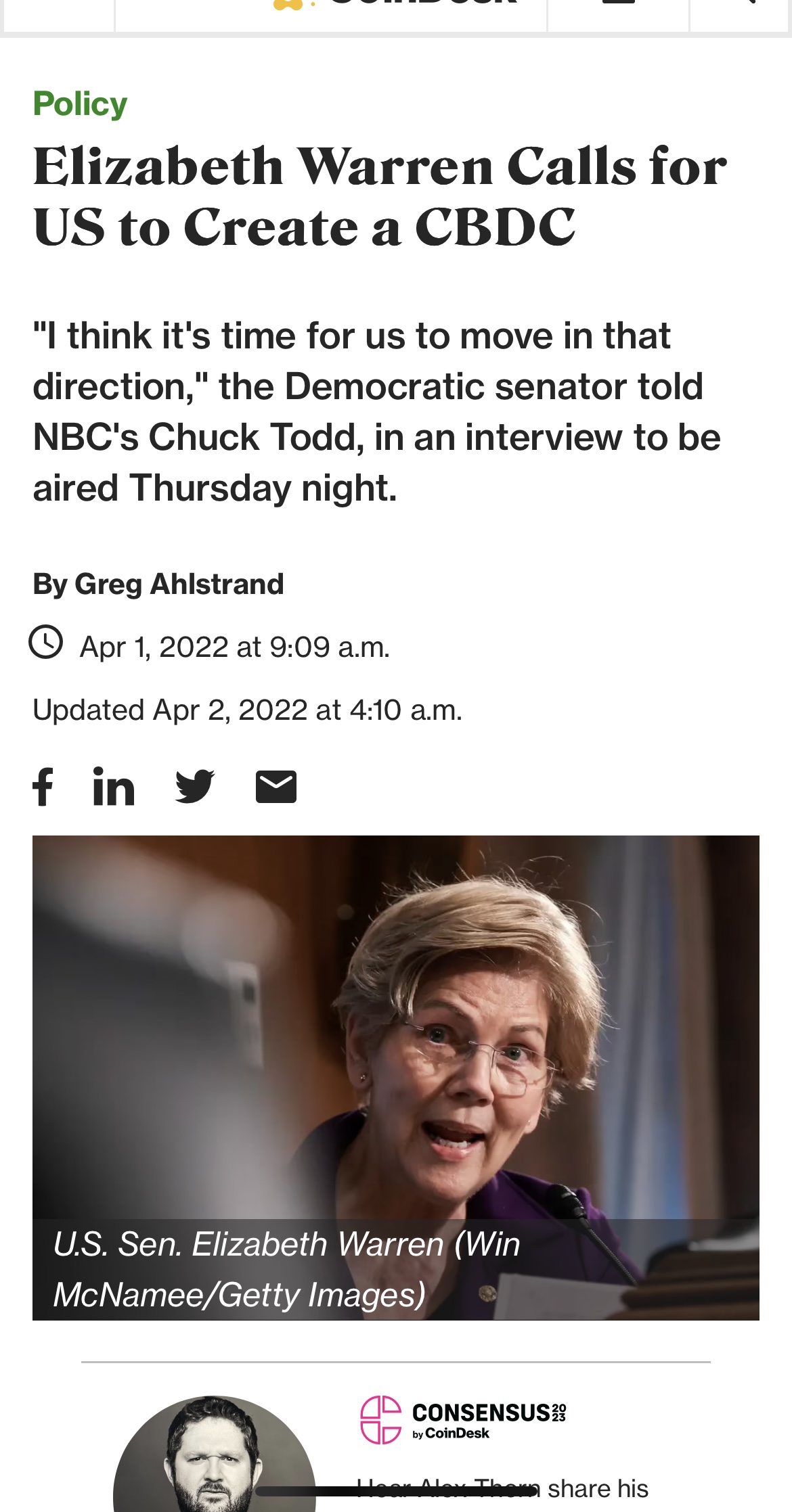
Wie aufs Stichwort treiben nun niederträchtige Opportunisten wie Elizabeth Warren die CBDC-Agenda offen voran und bilden Anti-Krypto-Koalitionen. Es bleibt nur die flackernde Erinnerung an Warrens scheinbar rechtschaffenen Kreuzzug gegen die Banken im Anschluss an 2008. Doch inzwischen ist auf widerliche Weise klar geworden, dass es ihr nie um die Befähigung des Einzelnen ging, sondern um mehr staatliche Kontrolle.
Und Senatorin-Karen ist nicht allein
EZB-Präsidentin Christine Lagarde bemüht sich, den digitalen Euro bis Oktober voranzubringen, und hat gerade angekündigt, eine Obergrenze von 1.000 Euro für Bargeld- und Kryptozahlungen einzuführen:
“Wenn wir uns nicht am digitalen Zentralbankgeld beteiligen […], riskieren wir, die Rolle des Ankers zu verlieren, die wir seit vielen Jahrzehnten gespielt haben.” Die Menschen sollen also ihr Geld digital halten, aber nicht mehr als 1.000 Euro online nutzen können. Die Angst der Politik ist geradezu greifbar.
Das liegt daran, dass es bei diesem neuen Gefühl der Dringlichkeit nicht nur um Bankenzusammenbrüche geht. Es wird wohl auch damit zu tun haben, dass die Finanzweltordnung auf den Kopf gestellt wird und jahrzehntelange Übereinkommen in Frage gestellt sind. Brasilien, Russland, Indien, China und Südafrika haben angekündigt, nicht mehr in Dollar, sondern in ihren Landeswährungen abzurechnen.
Gleichzeitig hat die OPEC gerade ihre Muskeln spielen lassen, indem sie ihre Ölproduktion freiwillig um mehr als 1 Million Barrel pro Tag gesenkt und damit die Inflation im Westen angeheizt hat. Dies veranlasste Japan, sich von den US-Verbündeten abzusetzen und unter Berufung auf seinen Energiebedarf russisches Öl zu kaufen, das über der Obergrenze von 60 Dollar liegt, die für die G7-Länder gilt. Der Machtverlust im Ausland veranlasst die westliche Führung dazu, die eigene Bevölkerung hart zu kontrollieren, um überhaupt ein gewisses Maß an Kontrolle über Fiskalpolitik zu behalten.
Denjenigen, die nicht bereit sind, sich in die Todeszellen der CBDCs und strenge Kapitalkontrollen treiben zu lassen, könnte die Zeit davonlaufen. Ich möchte nicht falsch verstanden werden: Grundsätzlich war es längst an der Zeit Währung und Zahlungen zu digitalisieren. Bitcoin ist diesen Weg gegangen und hat gezeigt, wie man wahre finanzielle Unabhängigkeit, Sicherheit und Freiheit erreichen kann. Doch die letzten 10-12 Jahre legten die Versäumnisse der Regierungen, die Marode des globalen Finanzsystem und den Unwillen der Zentralbanken offen, Macht zurück an die Menschen zu geben.
Es ist Zeit aufzuwachen und sich zumindest persönlich in Teilen von der Finanzpolitik der Zentralbanken, staatlichen und privaten Banken und der Regierung zu emanzipieren!
#Bitcoin now!
Wahnsinn ist wie Schwerkraft

Eine 2 Billionen Dollar Rettungsaktion für das Bankwesen! Die können nicht aufhören, Geld zu drucken. Das ist der grundsätzliche Schluss, die man hier ziehen muss.
Inflation sollte nicht real sein.
Aber die Preise steigen und jeder (!) auf der Welt merkt das in den letzten Jahren und Monaten deutlich.
Die Wirtschaft sollte stark sein.
Aber allein in diesem noch jungen Jahr 2023 wurden bereits 100.000 Beschäftigte in der Technologiebranche entlassen.
Der Finanzsektor sollte stabil sein.
Aber 2 der 3 größten Bankenzusammenbrüche der Geschichte fanden letzte Woche statt.
Die Rettungsaktion für die SVB sollte 25 Milliarden Dollar betragen.
Aber vier Tage später werden daraus 2 Billionen Dollar für den gesamten Finanzsektor.
Fällt hier noch jemandem ein Muster auf?
Die Regierungen und Zentralbanken können nicht aufhören Geld zu drucken.
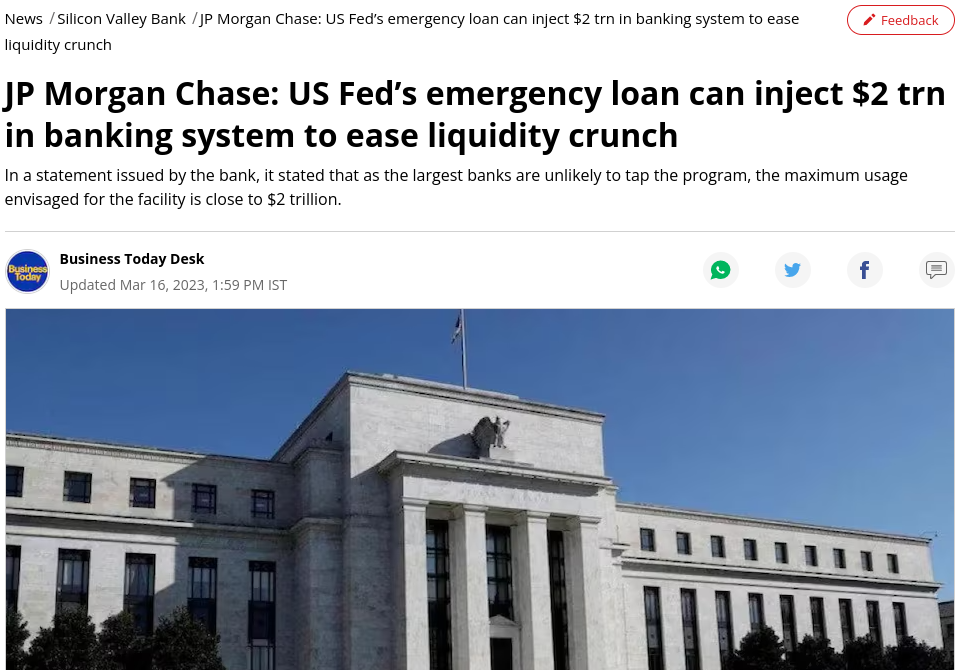
Wenn JP Morgan Recht hat, werden die 2 Billionen Dollar, die über das neue Kreditprogramm BTFP bereitgestellt werden, die Fed-Bilanz um 20 % erhöhen.
Das bedeutet 6’000 Dollar für jeden amerikanischen Mann, jede Frau und jedes Kind – neue Schulden.
Zufälligerweise wird jeder einzelne Schweizer Bürger in ähnlicher Weise 6’000 Dollar für die Rettungsaktion der Credit Suisse bezahlen – neue Schulden.
Das sind 54 Milliarden Dollar, die für eine einzige Bank mit einem Marktwert von 8 Milliarden Dollar versch(w)endet werden. Das ist ein Geschäft, das nur eine Regierung willig ist, einzugehen.
Muss uns das als Europäer denn interessieren? Es geht ja um amerikanische Banken und vielleicht um eine Schweizer Bank. Und überhaupt die Europäische Zentralbank …
Es ist ein Irrglaube, anzunehmen, das es in Europa “schon nicht so schlimm kommen wird”, dass es die Zentralbanken und Regierungen schon machen werden und, dass die Zinspolitik in Europa eine andere ist, usw …
Fakt: Gerade eben erst wurde in einer EZB-Ratssitzung eine Zinserhöhung auf 3,5 Prozent beschlossen.
Aber halt, es kommt noch besser.
Da es offenkunding wird, dass das gesamte Finanzsystem vollkommen auf der Unterstützung der Zentralbank wie auf riesigen Stelzen dahirstakst, werden viele Menschen unweigerlich falsche Schlüsse aus der “Rettung” ziehen.
Wir sehen nämlich nicht, dass das faule politische Gelder (also die inflationäre Geldpolitik an sich) die Ursache für die zunehmenden Misserfolg von Banken ist. Wir nehmen an, die müssten gerettet werden, um die Gelder der einfachen Menschen zu schützen. Doch wird damit der Bock zum Gärtner gemacht und die Menschen glauben an die die warme Umarmung der Zentralbank und hoffen gar darauf. Dabei rettet das marode System sich nur kurzfristig selbst – zu Lasten der Steuerzahler … und der Nicht-Steuerzahler … und der Kinder … und Arbeitslosen … und Rentner … und Arme …
Am Ende profitieren nur die Banken von einem direkten finanziellen Engagement, einer “Vertragspartei” oder einem Partner, der praktisch ausfallsicher ist, weil er sich im Zweifel immer neues Geld drucken kann und davon auch fleißig Gebrauch macht. Die Last trägt aber dann jeder durch die Inflation und steigenden Preise. Man sieht die direkte Verbindung nur nicht.
Warum aber sollten die Regierungen Interesse daran haben, gute und hart arbeitende Menschen davon auszuschließen, durch die Rettung des Finanzsystems zu profitieren?
Im Grunde wird der Normalbürger in finanzielle Abhängigkeit gebracht und ausschließlich als Konsument betrachtet. Konsument von Zahlungsdienstleistungen und zur Verfügung gestelltem Finanzmitteln gegen Bereitstellung von Arbeitskraft. Hier kommen sie ins Spiel, die “vertrauenswürdigen” CBDCs, also durch die Zentralbanken ausgegebene und verwaltete Digitale Währungen. Und die sind nicht nur schon voll in Arbeit, es werden auch schon jetzt die unterliegenden Strukturen zementiert, die CBDCs für den Bürger zwingend erscheinen lassen.
Wenn man darüber nachdenkt, sind Schatzämter der Regierungen schon heute eine Art von CBDC für Banken. Es ist aber so, dass nur Institutionen Zugang zu den Konten der Zentralbanken haben.
Aber was gut für die Gans ist, ist auch gut für den Gänserich
Es ist bestimmt kein Zufall, dass die Fed erst vor kurzem angekündigt hat, dass ihr aufregender neuer FedNow Service im Juli seinen Betrieb aufnehmen wird. Toll, oder? Man müsste jetzt noch wissen, was das ist.
Der FedNow Service wird es Finanzinstituten – unabhängig von ihrer Größe oder geografischen Lage – ermöglichen, rund um die Uhr und an jedem Tag des Jahres landesweit Sofortzahlungsdienste anzubieten. Also Banken können global zu jeder Zeit Sofortzahlungen anbieten. Das hört sich erstmal super an, wie ein Kind von VISA und Paypal auf Steroiden. Aber die wahren Eltern sind Regierungen und Zentralbanken und genau die werden die Kontrolle über die Geldmenge in eine Virtuelle Umgebung verlagern – außerhalb der Reichweite der Normalbürger und eingebettet in ein marodes Finanzsystem. Ein “Schuldscheinsystem” außerhalb der Kontrolle des Nutzers.
Wird die nächste Krise FedNow für die breite Öffentlichkeit erzwingen?
“Wahnsinn ist wie Schwerkraft: Man braucht nichts weiter als einen kleinen Schubs.”
Heath Ledger in “The Dark Knight” (2008)
Inflation auf dem Vormarsch

Inflation, Geldwerteverfall und Weltwirtschaftskrisen sind aktuell wichtige Themen, die jeden Verbraucher betreffen können. Eine stark steigende Inflation führt zu einem Verlust von wohlstand, da das Geld an Kaufkraft verliert und die Preise für Güter und Dienstleistungen steigen.
Historisch gesehen haben sich Inflationsspitzen häufig in Zeiten wirtschaftlicher Instabilität und Krise gezeigt, wie beispielsweise während der Großen Depression in den 1920er und 1930er Jahren. Eine wirtschaftliche Krise kann zu einer Verknappung von Gütern und Dienstleistungen führen, was wiederum die Inflation ankurbelt.
In slchen Zeiten können alternative Anlagen wie Gold und Kryptowährungen wie Bitcoin eine Möglichkeit sein, den Wert des Vermögens zu schützen. Gold gilt als eines der ältesten und bewährtesten inflationssichere Anlagen, aber es kann auch von Regierungen beschlagnahmt oder konfisziert werden. Bitcoin hingegen ist eine dezentralisierte Kryptowährung, die nicht durch Regierungen oder Finanzinstitute kontrolliert wird. Dies bietet ein gewisses Maß an Unabhängigkeit und Privatsphäre, da Regierungen den Besitz von Bitcoin nicht einschränken oder beschlagnahmen können.
Es ist wichtig, sich über die Risiken und Chancen von Inflation, Geldwerteverfall und Weltwirtschaftskrisen sowie alternative Anlagen wie Gold und Bitcoin im Klaren zu sein. Daher empfehle ich natürlich, sich vor jeder Investition gründlich zu informieren und die eigene finanzielle Situation sorgfältig zu berücksichtigen. Aber im Grunde hat man bei der aktuellen starken Inflation ja schon bald das Gefühl, dass man es sich nciht leisten kann, auf eine Wertanlagen wie Bitcoin zu verzichten.
Chinesische Feiertage 2023
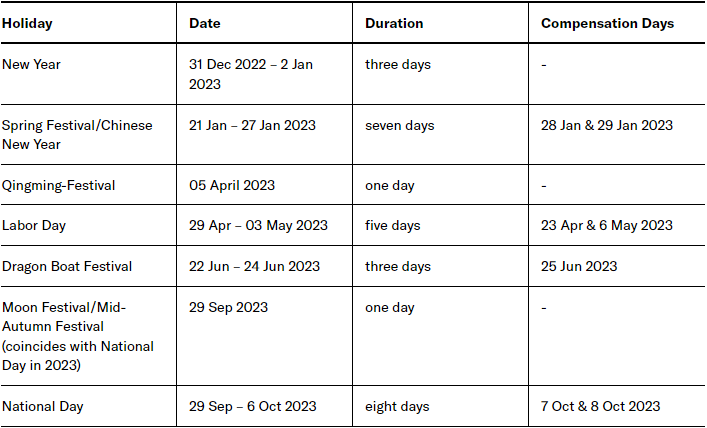
New Year
- December 31, 2022 to January 2, 2023 (three days in total; Saturday to Monday)
Spring Festival (Chinese New Year)
- January 21 to 27, 2023 (seven days in total; Saturday to Friday)
- Adjusted working days: January 28, 2023 (Saturday) and January 29, 2023 (Sunday)
Tomb Sweeping Festival (Ching Ming Festival)
- April 5, 2023 (one day in total; Wednesday)
Labor Day
- April 29 to May 3, 2023 (five days in total; Saturday to Wednesday)
- Adjusted working days: April 23, 2023 (Sunday) and May 6, 2023 (Saturday)
Dragon Boat Festival
- June 22 to 24, 2023 (three days in total; Thursday to Saturday)
- Adjusted working days: June 25, 2023 (Sunday)
Mid-Autumn Festival and National Day
- September 29 to October 6, 2023 (eight days in total; Friday to Friday)
- Adjusted working days: October 7, 2023 (Saturday) and October 8, 2023 (Sunday)
An idealist’s and a maximalist’s hope
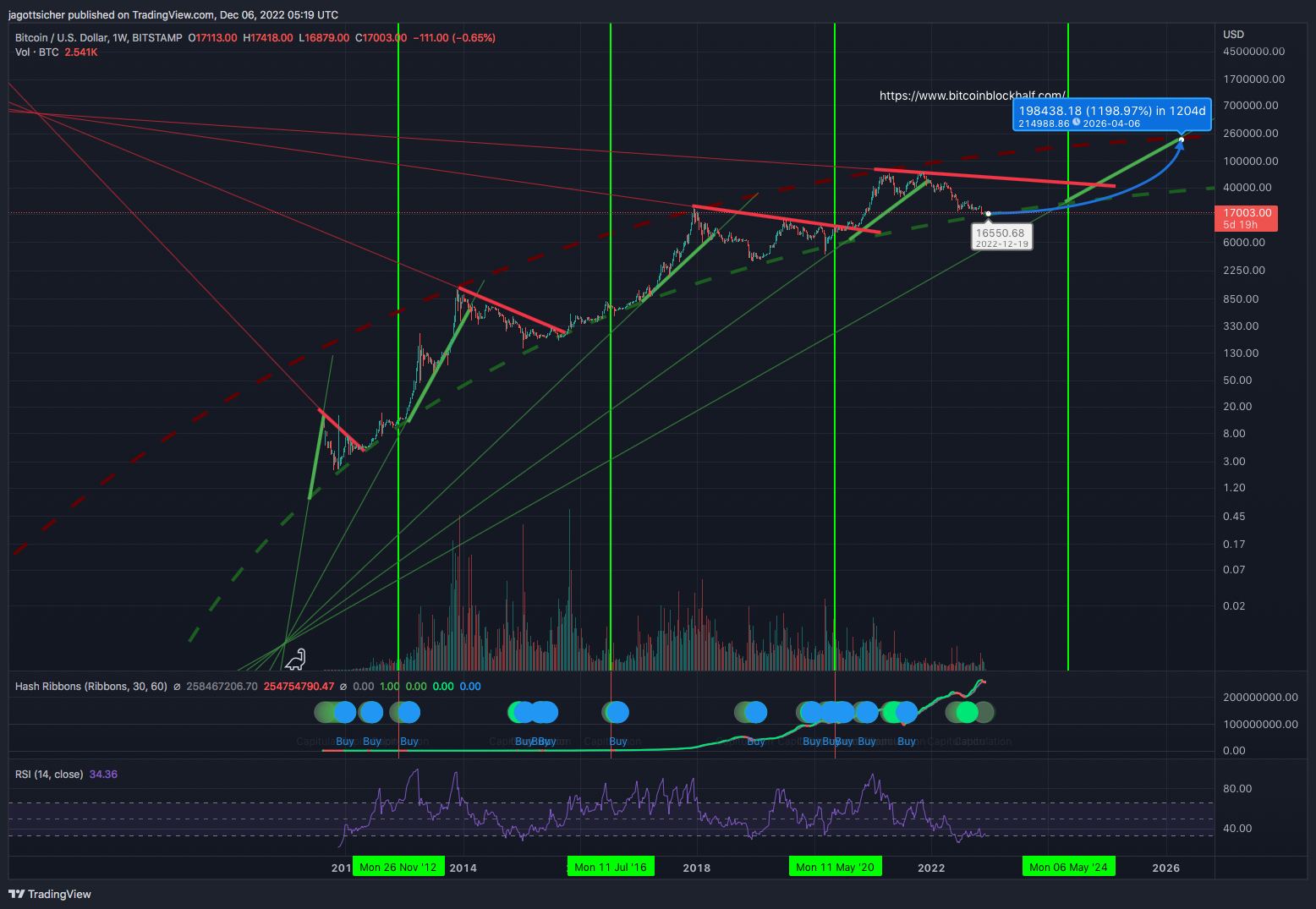
I am not a trader but an idealist and a maximalist.
New horizon for end of crypto winter and the start of the next (5th) bull circle.
Goal: Sell at 200k, depending on #inflation for #fiat maybe better to stay in #Bitcoin!
Feel free to checkout my … https://bit.ly/3iyM7L3
#wp
I am not a trader but an idealist and a maximalist.New horizon for end of crypto winter and the start of the next (5th) bull circle.
Goal: Sell at 200k, depending on #inflation for #fiat maybe better to stay in #Bitcoin!
Feel free to checkout my … https://bit.ly/3iyM7L3
— Jens Schendel⚡️ (@jagottsicher)
Dec 6, 2022
Alexander, der Große und Bitcoin: Der Gordische Knoten der Fiat-Währungen

Es ist unglaublich, was die Welt vergißt und – was sie nicht vergißt.
Marie von Ebner-Eschenbach (1830 – 1916)
Der überwiegende Teil menschlicher Erfahrung und Erkenntnis wird auf den Müllhaufen der Geschichte verbannt und dort gnadenlos vergessen. In vielen Fällen vielleicht zu Recht. Augenscheinlich ist das Leben weitgehend banal und von Nichtigkeiten durchsetzt.
Aber die wenigen Geschichten, die überleben, überleben aus einem gutem Grund. Sie sprechen uns auf einer tieferen Ebene an. Sie berühren eine grundlegende und dauerhafte Wahrheit über das Dasein des Menschen. Es sind keine Geschichten aus einer weit zurückliegenden Vergangenheit, es sind Geschichten über das Hier und Jetzt – aus der Gegenwart. Die Namen und Gesichter mögen sich ändern, aber die Geschichten bleiben dieselben. Wir können nicht anders, als sie immer und immer wieder zu spielen, Generation für Generation. Sie sind für uns heute so relevant wie eh und je. Diese Geschichten bielden die Grundlagen für Legenden, denn sie verschiedenen Versionen brennen sich als Archetypen in unser universelles Gedächtnis ein.
Im Gegensatz dazu mag Bitcoin wie eine bahnbrechende neue Technologie ohne historische Parallelen erscheinen. Aber in Wahrheit passt Bitcoin in eine viel reichhaltigere und bedeutungsvollere Geschichte über unsere menschliche Natur. Lassen Sie uns nun in eine solche Geschichte eintauchen und erkunden, wie Bitcoin in ihrer aktuellen Aufführung auf der Weltbühne eine Schlüsselrolle spielt.
Alexander der Große, der mit seiner Speerspitze ein riesiges Reich schuf und dessen Taten zum Stoff der Legende geworden sind, gehört zweifellos zu den wenigen Figuren, die den Herausforderungen der Zeit überstanden haben. Eine seiner Legenden sticht dabei besonders hervor. Der antike griechische Mythos erzählt, wie Alexander der Große auf seinem ehrgeizigen Feldzug durch Westasien in die phrygische Hauptstadt Gordium in der heutigen Türkei gelangte.
Phrygien, so die Geschichte, war ein Königreich ohne König. Die Einwohner glaubten, dass der rechtmäßige Thronfolger erst noch bestimmt werden müsse. Der wahre König würde sich selbst offenbaren, indem er ein unlösbares Problem – den gordischen Knoten – löste. Dieser Knoten war ein alptraumhaftes Gewirr aus handtellergroßer Maisrinde, das sich um das Joch eines Ochsenkarrens gewickelt hatte und nicht mehr zu lösen war.
Der Ochsenkarren gehörte dem alten König Gordias, der, selbst ein einfacher Bauer, vor tausend Jahren durch Vorsehung auf den Thron gesetzt worden war. Eine Prophezeiung sagte voraus, dass derjenige, der den Knoten lösen könnte, nicht nur als Nachfolger des toten Königs über Phrygien herrschen, sondern auch ganz Asien erobern würde. Das reizte natürlich Alexander den Großen, der die Herausforderung gerne annahm.
Als es ihm jedoch nicht gelang, den Knoten zu entwirren, wie es alle vor ihm getan hatten, tat er etwas, das die Phryger schockierte.
Er zückte sein Kurzschwert und zerschnitt kurzerhand die Seile mit den Worten:
“Es macht keinen Unterschied, wie sie gelöst werden.”
Der interessante Teil der Geschichte
Alexander der Große hatte eindeutig gegen die Prophezeiung des Orakels verstoßen, indem er den Knoten durchtrennte, anstatt ihn zu lösen, und hatte damit eine heilige Reliquie auf den Stufen ihres Tempels entweiht. Doch wie reagierten die Phryger?
Sie krönten ihn auf der Stelle zum König. Wie kann das sein?
Obwohl die Mythologie des gordischen Knotens weithin bekannt ist, wird sie nur allzu oft zutiefst missverstanden.
Viele Historiker und Philosophen ziehen daraus einige der folgenden Schlüsse:
- Dass manchmal die beste Antwort auf ein komplexes Problem die einfachste ist.
- Dass manche Probleme nur durch kühnes Handeln und mit großem Ehrgeiz zu lösen sind.
- Dass Alexander der Große die Worte der Prophezeiung auf seine Weise umgangen hat. Denn besonders kluge Menschen sehen Lösungen, wo andere sie nicht sehen. “Über den Tellerrand schauen”, würden wir das nennen.
All diese Interpretationen gehen jedoch am Ziel vorbei und verkennen eine grundlegende Wahrheit, die die Geschichte auf elegante Weise offenbart. Der Kern der Legende ist ganz einfach der folgende:
Alexander der Große war vielleicht der größte Eroberer und Kriegsherr aller Zeiten. Er steht sicherlich in einer Reihe mit Attila dem Hunnen, Sun Tzu, Saladin, Julius Cäsar und Hannibal Barca. Er war in Schlachten unbesiegt und hatte den größten Teil der zivilisierten Welt in die Knie gezwungen. Außerdem hatte er ein Heer treuer mazedonischer Soldaten im Rücken, die vor den Toren von Gordium auf ihn warteten und bereit waren, die Stadt im Handumdrehen zu plündern und zu brandschatzen. Wer von den Phrygern würde es wagen, die Methoden Alexanders des Großen in Frage zu stellen? Wenn er die Regeln auf die leichte Schulter nehmen wollte, wer sollte ihm da widersprechen?
Und so ist der gordische Knoten in seinem Kern die Geschichte, in der Macht Recht schafft.
Es ist kein Zufall, dass Alexander der Große sein Schwert benutzte, um das Problem zu “lösen”.*
Aber der gordische Knoten hat uns eine noch tiefere Lektion zu erteilen. Um seine Bedeutung zu verstehen, müssen wir zunächst die Botschaft der Geschichte als das begreifen, was sie wirklich ist.
In der Geschichte war der Knoten um einen Ochsenkarren geschlungen – eine Technologie für Transport und Handel und ein Symbol für Zivilisation und Ordnung. Wie die Prophezeiung voraussagte, würde der rechtmäßige König den Ochsenkarren losbinden und Herrscher über die bekannte Welt werden. Dies würde durch den Einsatz von roher Kraft geschehen – durch das Schwert. Wie um diesen Punkt zu verdeutlichen, haben viele historische Gemälde und künstlerische Darstellungen seither einen Streitwagen anstelle eines Ochsenkarrens abgebildet. Der Streitwagen ist natürlich ein eindrucksvolles Symbol für Krieg und Triumph.
Die Botschaft ist klar: Wenn eine Situation so verworren und verwickelt ist, dass sie unhaltbar wird, ein sprichwörtlicher gordischer Knoten, dann braucht es einen energischen Akteur, der die alten Regeln über Bord wirft und damit eine neue Ordnung schafft.
Was aber, wenn es keinen weisen und mächtigen Führer gibt, der das Schwert in die Hand nimmt und das Notwendige tut?
Schließlich sind die Alexander der Große dieser Welt in den langen Bögen der Geschichte selten und weit entfernt. Sie sind die Ausnahmen, nicht die Regel. Aus diesem Grund hat Alexander der Große selbst nie einen Erben für sein eigenes Reich bestimmt – wozu auch? Als er auf dem Sterbebett gefragt wurde, an wen sein unermesslicher Reichtum und sein ausgedehntes Reich fallen würden, antwortete er einfach: “An den Stärksten.”
Was folgte, waren fünfzig Jahre Krieg
Diese Zahl hat eine Bedeutung, auf die wir noch zurückkommen werden. Der Punkt ist jedoch, dass der gordische Knoten nicht immer mit einem sauberen klaren Schnitt gelöst werden kann, sondern er oft mit brutalen Mitteln ausgefranst wird.
Zu diesem Zweck hatten beispielsweise die Römer ihre eigene Methode entwickelt, um einen gordischen Knoten zu durchtrennen, wann immer er sein hässliches Haupt erhob. Die Bürger der Arbeiterklasse verließen aus Trotz ganze Städte, die so genannte “Plebejer-Nachfolge”, und überließen es den Herrschern, sich untereinander zu streiten und einen Systemwechsel zu erzwingen.
Das ist nichts Neues. Solche Übergänge und Transformationen der GEsellschaft finden mit erstaunlicher Regelmäßigkeit statt – etwa alle fünfzig Jahr. Die Geschichte lehrt uns, dass gesellschaftliche Ordnungen in der Regel etwa drei Generationen brauchen, bis sie zu einem gordischen Knoten verkommen und einen Alexander den Großen benötigen, um sie zu durchtrennen. Wie das Sprichwort sagt: Die erste Generation sät ihn, die zweite lässt ihn wachsen, und die dritte sprengt ihn. Das ist eine Geschichte, die so alt ist wie die Zeit.
Dieser Prozess des zivilisatorischen Verfalls und der Wiedergeburt ist ein so tief verwurzeltes und menschliches Phänomen, dass er sogar seinen Weg in die Heilige Schrift gefunden hat. Das Buch Levitikus schreibt ein sogenanntes Jubeljahr als Heilmittel für diese Säuberungen vor. Das Jubeljahr findet einmal alle fünfzig Jahre statt und ist eine besondere Zeit, in der alle Schulden vergeben und alle Schiefertafeln abgewischt werden – ein großer Neuanfang:
“So sollst du das fünfzigste Jahr einweihen und allen Bewohnern des Landes eine Befreiung verkünden. Es soll ein Jubeljahr für dich sein (Levitikus 25:1-4, 8-10, NASB).”
Ja, die Namen und Gesichter mögen sich ändern, aber die Geschichte ändert sich nicht. Und wir befinden uns heute wieder an einem solchen Wendepunkt. Ein Paradigmenwechsel steht bevor oder hat bereits stattgefunden!
Die derzeitige Finanzweltordnung besteht seit etwas mehr als fünfzig Jahren, und jetzt bricht sie aus allen Nähten (was für ein Zufall!). Dieser jüngste Zyklus begann mit der Abschaffung des Goldstandards am 15. August 1971. Seit der Abschaffung des Goldstandards lebt die Welt nur noch von Papiergeld, Krediten und geliehener Zeit. Seitdem leben wir in einem globalen Fiat-Experiment. und im Prinzip leben wir auf Pump!
Doch dieses Kapitel neigt sich gerade drastisch schnell seinem Ende zu. Schließlich ist unser derzeitiges Finanzsystem der gordische Knoten von allen, und wir stehen zweifelsohne an der Schwelle zu einem Reset.
Die Finanzkrise von 2008 bot nur einen winzigen Vorgeschmack auf das, was noch kommen wird. Als das Kartenhaus im April jenes Jahres in sich zusammenzufallen begann, dämmerte unserer herrschenden Klasse endlich eine erschreckende Erkenntnis: Das Gewirr aus Schulden, hypothekarisch gesicherten Wertpapieren und anderen kreditbasierten Derivaten war zu einem Monstrum mutiert, das alles einschnürte und erstickte. Schlimmer noch, die Finanzkrise offenbarte, wie Billionen von Dollar an schuldenbasierten Derivaten Ansteckungseffekte verursachten, die niemand wirklich verstand – die Eigentumskette des Systems war nicht mehr nachvollziehbar.
Eine Fallstudie von EJ Schoen erklärt, wie:
“…niemand wusste, wer wem Geld schuldete oder wie viel geschuldet wurde, was dazu führte, dass die Banken aufhörten, anderen Banken zu vertrauen und Kredite zu vergeben.”
Und als das Vertrauen in das System schließlich am 29. September 2008 seinen Tiefpunkt erreichte, fiel der Dow um sieben Prozent und markierte damit den größten Tageseinbruch in der Geschichte. Dies war der Versuch der Plebejer, den Knoten zu lösen. Es waren nicht die römischen Bürger, die aus ihrem Kapital flüchteten, sondern die Investoren, die versuchten, das Schiff zu verlassen, indem sie alle Positionen verkauften.
Aber zu Zeiten des Römischen Reiches gelang es den Plebejern letztlich nicht, den unvermeidlichen Zusammenbruch Roms aufzuhalten, und sie mussten hilflos mit ansehen, wie korrupte Zentralplaner die Währung entwerteten und ein einstmals großes Reich in den Ruin trieben und ausplünderten. Im Laufe einiger schmerzhafter Jahrzehnte wurde die Hauptstadt praktisch leergefegt und stürzte von mehr als einer Million Einwohnern auf nur noch ein paar Tausend Einwohner ab. Die Plebejer konnten nicht verhindern, dass die zivilisierte Welt in jahrhundertelange Finsternis stürzte.
Und so wie die Plebejer versagt hatten, so hatten auch wir versagt. In Ermangelung eines Alexanders des Großen wurde der Knoten nicht durchgeschlagen. Das Gegenteil war der Fall. Der Knoten wurde noch fester, als die Bürokraten Milliarden von gedrucktem Geld in die Leere schütteten. Die vermeintliche Lösung für die globale Finanzkrise bestand darin, das System mit zusätzlichen Schulden zu überziehen. Seitdem haben die Zentralbanken den Markt immer weiter gestützt, indem sie die Geldmenge aufblähten und die Währung weiter entwerteten.
Und jetzt ist der Knoten so verdreht, dass selbst etwas so Einfaches wie Aktien, ein vermeintlich unkomplizierter Ausdruck von finanziellem Eigentum, zu einem unüberschaubaren Gewirr von Schulden geworden ist:
Die DTCC, der weltweit wichtigste Handelsabgleichsdienst, zieht 99 Prozent des US-Handelsflusses an und soll den Überblick darüber behalten, wer was besitzt.
Nur, das können sie nicht.
Wie wir inzwischen wissen, haben Dutzende von Gerichtsverfahren ergeben, dass die im Umlauf befindlichen Aktien bei Tausenden von Unternehmen den tatsächlichen und genehmigten Bestand übersteigen.
So kommt es, dass GME einen Short-Anteil von 149 % hatte (was unmöglich ist!) und dass Aktionäre 33 % mehr Dole Foods-Aktien besaßen, als es Dole Foods-Aktien gab.
Der Knoten hat sich unvorstellbar verheddert
Hier können wir den Bogen zurück schlagen zur Geschichte von Alexander dem Großen: Die Handlung ändert sich nie – nur die Namen und Gesichter sind andere. Und so wird der Gordische Knoten auf die eine oder andere Weise aufgelöst. Sei es durch die Hand eines mächtigen Anführers, der die Welt wieder in Ordnung bringen kann, oder unter der Last seines eigenen erdrückenden Eigengewichtes, das alle Welt ins Chaos stürzt.
Doch es gibt einen großen Unterschied: Zum ersten Mal müssen wir nicht mehr auf einen Alexander den Großen warten. Stattdessen können wir das Schwert selbst schwingen. Aufgrund der einzigartigen Eigenschaften von Bitcoin, sich selbst zu verwahren, können wir den gordischen Knoten jederzeit durchschlagen, indem wir einfach unser eigenes Geld in Besitz nehmen und die Verantwortung für unseren Wohlstand und die Verwahrung unserer Werte selbst übernehmen.
Vorbei sind die endlosen und nebulösen Ketten des kreditbasierten Eigentums. Der einfache Akt der Inbesitznahme des eigenen Geldes verbannt alle Mittelsmänner, setzt das sich endlos vermehrende Papiergeld in Brand und klärt das wahre Eigentum. Die Plebejer haben nun endlich ein Werkzeug, um den Knoten selbst zu durchschlagen. Und während sich Bitcoiner selbst als “Plebs” bezeichnen mögen, ist es höchste Zeit, dass wir auch verstehen, dass Bitcoin das Schwert ist.
Bitcoin ist das Werkzeug, das mit einem Hieb den Gordischen Knoten aus Schulverschreibungen, Inflation, nicht nachvollziehbaren Kreditsicherungen und zweifelhaften Bewertungen zerschlagen kann.
* Eine alternative und weit weniger bekannte Version des Mythos besagt, dass Alexander der Große den Knoten löste, indem er den Splint aus dem Joch zog. Diese Version hat jedoch den Test der Zeit nicht überstanden und stattdessen hat sich der Ausdruck “den gordischen Knoten durchschlagen” in unseren Wortschatz eingeprägt.