First of all: According to Chinese law (including the CSL — the Cybersecurity Law) and China Telecom’s Terms and Conditions the following instruction is certainly not intended to be executed in China, with high probability illegal and prosecution by the authorities cannot be excluded. I decline any responsibility for the consequences.
In China, China Telecom’s internet connection usually comes with non-transparent access via a combination of modem and router (including 3 or 4 LAN ports). The modem uses a DHCP client to get a public IP assigned via ADSL or fiberglass. If required, the integrated router uses a DHCP server to set up a network in the 192.168.1.x segment. The modem/router reserves itself the IP 192.168.1.1 and serves as gateway and DNS in the intranet.
A total of 253 clients can log on via LAN ports and WiFi (ID 2 to 254). If you want to set up additional networks within your apartment, you can connect additional routers to each LAN port.
The problem
In case of doubt, you might find your devices even be behind two NAT masquerades, but you only have control over one. Port forwarding and port triggering end at China Telecom’s modem/router combination. However, it is possible to switch the modem to bridge mode and operate it standalone. A technician comes out and manipulates the modem. Now, however, the internal router can no longer be used and you have to connect your own router to the modem. After that, only one router can be operated with the modem. The internal LAN ports are useless then. But at least you get your access data to the network of China Telecom from the technician. For most people that should be the easier and legal way to gain control over the routing tables.
I had the bridge mode switched on temporarily, but couldn’t make it clear to the technician that I wanted to operate a router a few meters away and not behind the wall panel. Either he lacked the imagination, but my wife’s attempts at mediation and translation rather indicate that he assumed that a private customer did not have the technical knowledge to operate a router independently (or even several in one apartment). Anyway, I let the modem run unbridged again. In the short time, I could not try out whether it would be possible in bridge mode to address a certain computer under a certain port behind the NAT under the public IP. My only goal was to get control over the port forwarding and the internal firewall of the modem/router.
On the modem itself, there is a sticker with the credentials for the customer to log on to the router — usually the user useradmin and a 5-digit combination of numbers and letters. The settings for useradmin are very limited and port forwarding between public IP and IP assigned by DHCP in the intranet is completely disabled. Therefore also DynDNS services do not work in China.
Access to the modem as user ‘telecomadmin’ promises further options. The password seems to be an 8 to 10-digit combination of numbers and letters, but after several unsuccessful logins, the router prohibits further login attempts for several minutes. Brute-force attacks may be possible, but seem to be time-consuming. Anyway, I prefer a set of lockpicks to a crowbar.
In the past, a user useradmin could create a dump of the modem settings in which the telecomadmin’s password was stored as plain text. After waiting for you some time stopping facepalming I’ll tell you that this is definitely not possible anymore but shows the lax handling of China Telecom’s hardware security settings. However, access via a serial interface appeared even more promising, although the connectors were not made externally accessible. To get access to the pins the case has to be opened which results in a loss of warranty. How good, if you already have experience with logging the serial service interfaces on a WRT54G and some ASUS routers.
Physical — let’s get physical …
Armed with an adapter kit for reading serial data I started to work. In the absence of a computer with a RS232 interface, I took an additionally RS232 to USB converter to hand. You only have to loosen two screws, one of which is covered by a sticker. Stickers can be easily loosened and later they have properly stuck on again. The case can be opened damage-free with a spatula and some skill.

A jailbreak for a China Telecom modem simply means finding out the password for the user telecomadmin, who can finally change all settings on the modem. While the term “jailbreak” suggests the idea of breaking out of a prison, it means nothing more than hacking the device. China Telecom seems to rely entirely on the ignorance and technical inability of its customers. Since I have put on the white hat here and only planned the private (test) operation of several Lighting Network nodes behind a NAT firewall, I don’t think my action attracted the attention of the gatekeepers.
I don’t know what other routers/modems China Telecom ships, but I assume that they are all configured very similarly. The software which allows access to the backend is from 2012.
PAWNED!
After opening the case you find some lonely but properly labeled pins for maintenance purposes. You connect
GND/GND,
TXD/RXD, and eventually
RXD/TXD to connect your router through adapter with your computer.
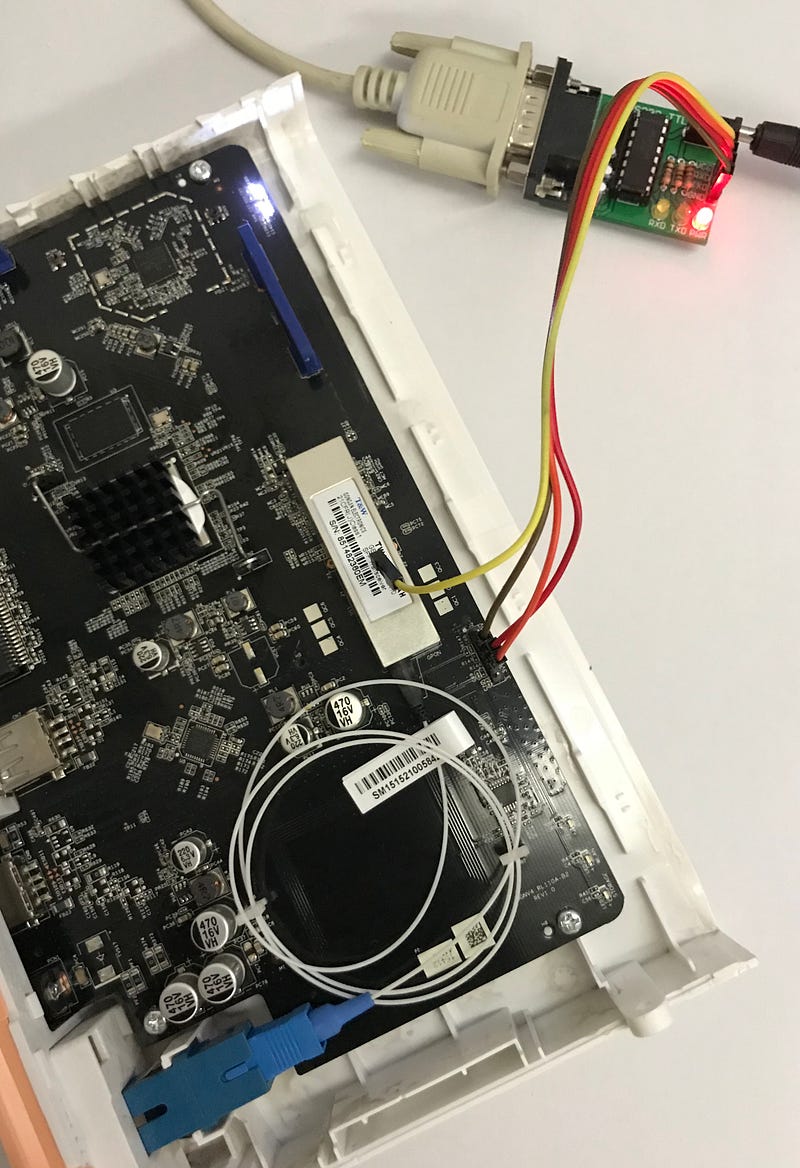
Whatever adapter device and operating system you may use the driver will provide access to a (virtual) COM port. I used windows and plugging in the adapter and installing the driver results in a note that the device was accessible by COM port com4.
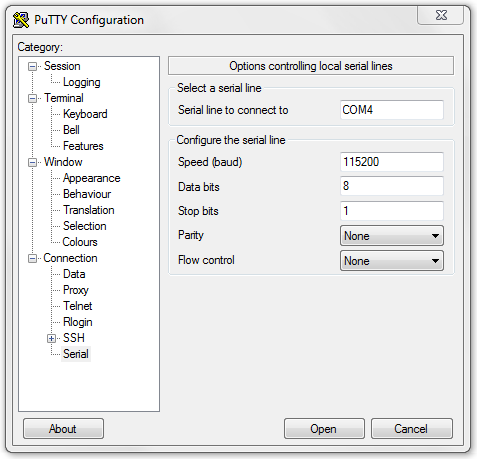
Open a terminal (I used putty) with setting like this:
After powering on the router the console is spammed with the modem’s, respectively router’s log.
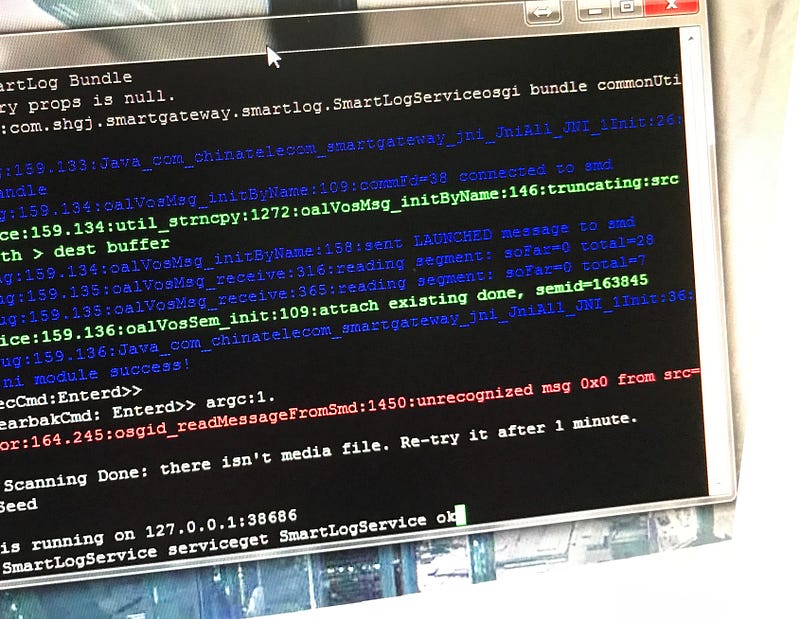
You can stop that by pressing the return button. A prompt is shown to enter a username and password. It was hard to believe but the first try of the combination admin/admin worked fine. Your prompt shows ‘S304’ which is a usual ‘user’ for a router like this.
With the command
show mdm config
you can force the machine to dump all the system config. Rightclick upper left corner of putty and select “copy all to clipboard” and eventually paste in the editor of your choice. Mine was notepad++.
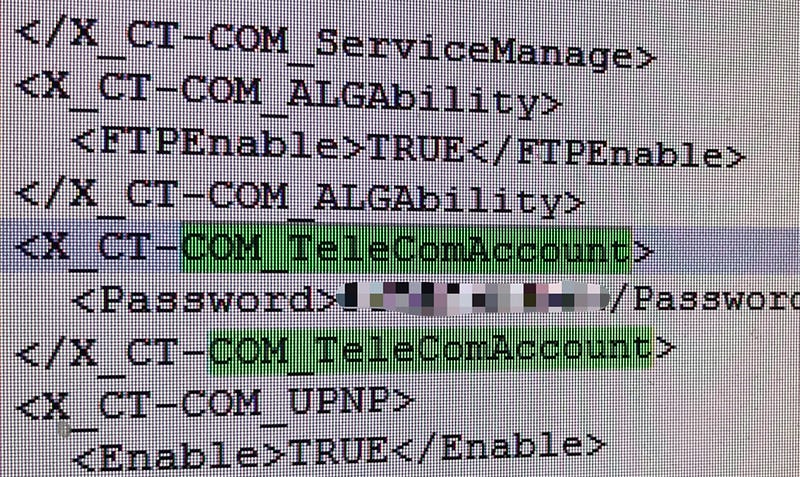
Then search for the term
COM_TeleComAccount
You will get the super admin password
…
XXXXXXXXXX
…
Login with
telecomadmin/XXXXXXXXXX
Now we get the super admin control panel, lean back, and enjoy satisfaction to have been a little bit smarter than China Telecom.
The bottom line is that …
Again, this procedure is certainly not legal in China! As far as I know, the entire internet traffic in China is subjected to a Deep Packet Inspection (DPI), but China Telecom apparently does not spend much importance to the security of devices provided by them. Standard usernames and password combinations, cleartext password in plain text files which every owner of a screwdriver can access and the complete lack of any state-of-the-art encryption make it easy as ABC to jailbreak their hardware.
I published this article first on MEDIUM.
I operate my own little Lightning Node
Feel free to open a channel e.g. with
clightning
lightning-cli connect 0366217f4a7abf70842f794e94a4cbddc249d5cbaf9c0ffd0b7e4638d9bf07845d 81.7.17.202 9735
lnd
lncli connect 0366217f4a7abf70842f794e94a4cbddc249d5cbaf9c0ffd0b7e4638d9bf07845d@81.7.17.202:9735
eclair
eclair-cli connect 0366217f4a7abf70842f794e94a4cbddc249d5cbaf9c0ffd0b7e4638d9bf07845d@81.7.17.202:9735
(please be note that you have to remove hyphens from the line above, after copy/paste somewhere) or try my already working online tipping tool. Check it out! Send me some Satoshis throught the Lightning ⚡️ Network (beta, but fast as lightning!)

