#ShowYourStripes now!
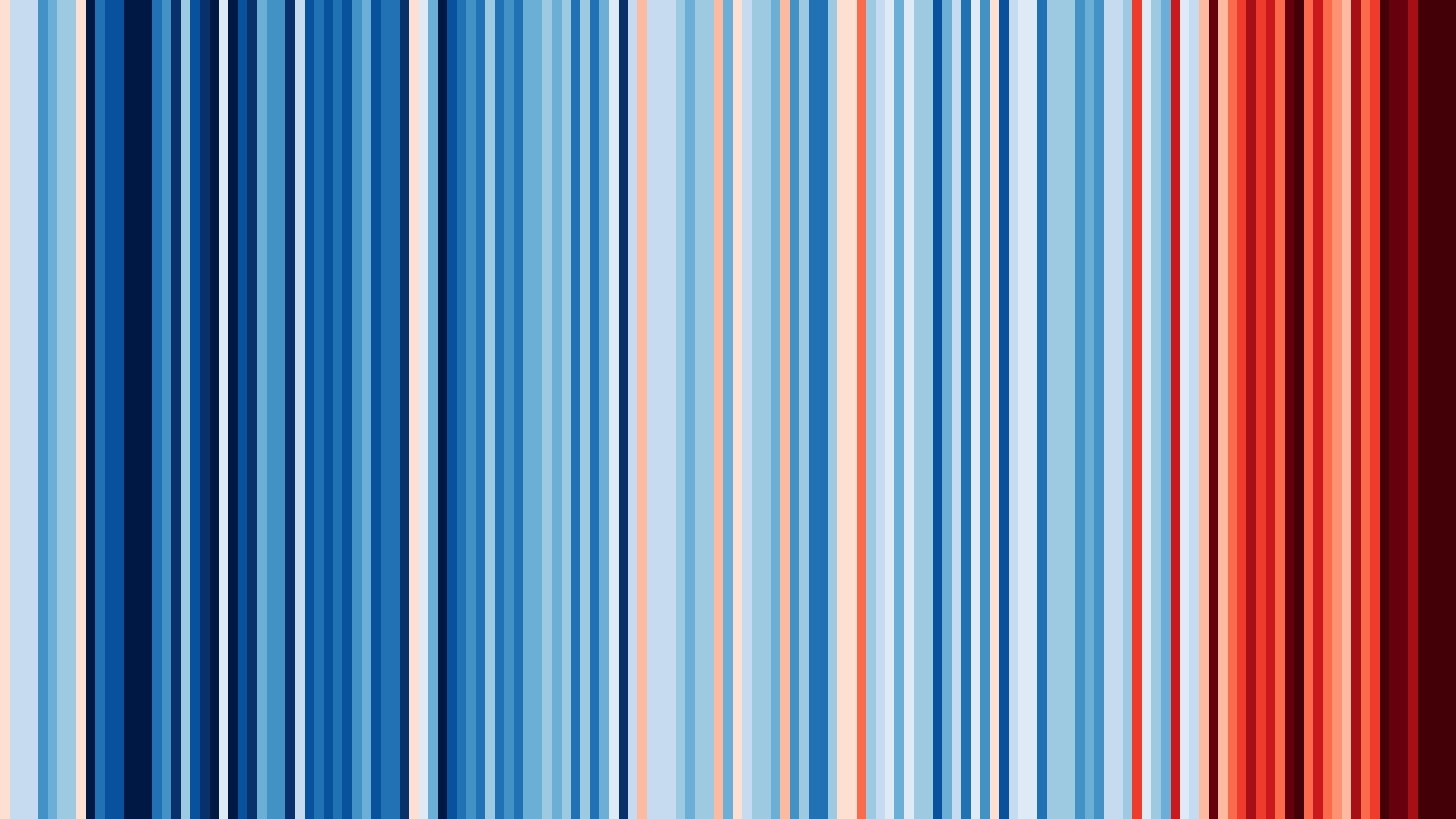
#ShowYourStripes illustrates the climate change for your region from 1850 to today!
This is for Shanghai!
Checkout the specific temperature changes by visiting showyourstripes.info
Chinesische Feiertage 2024
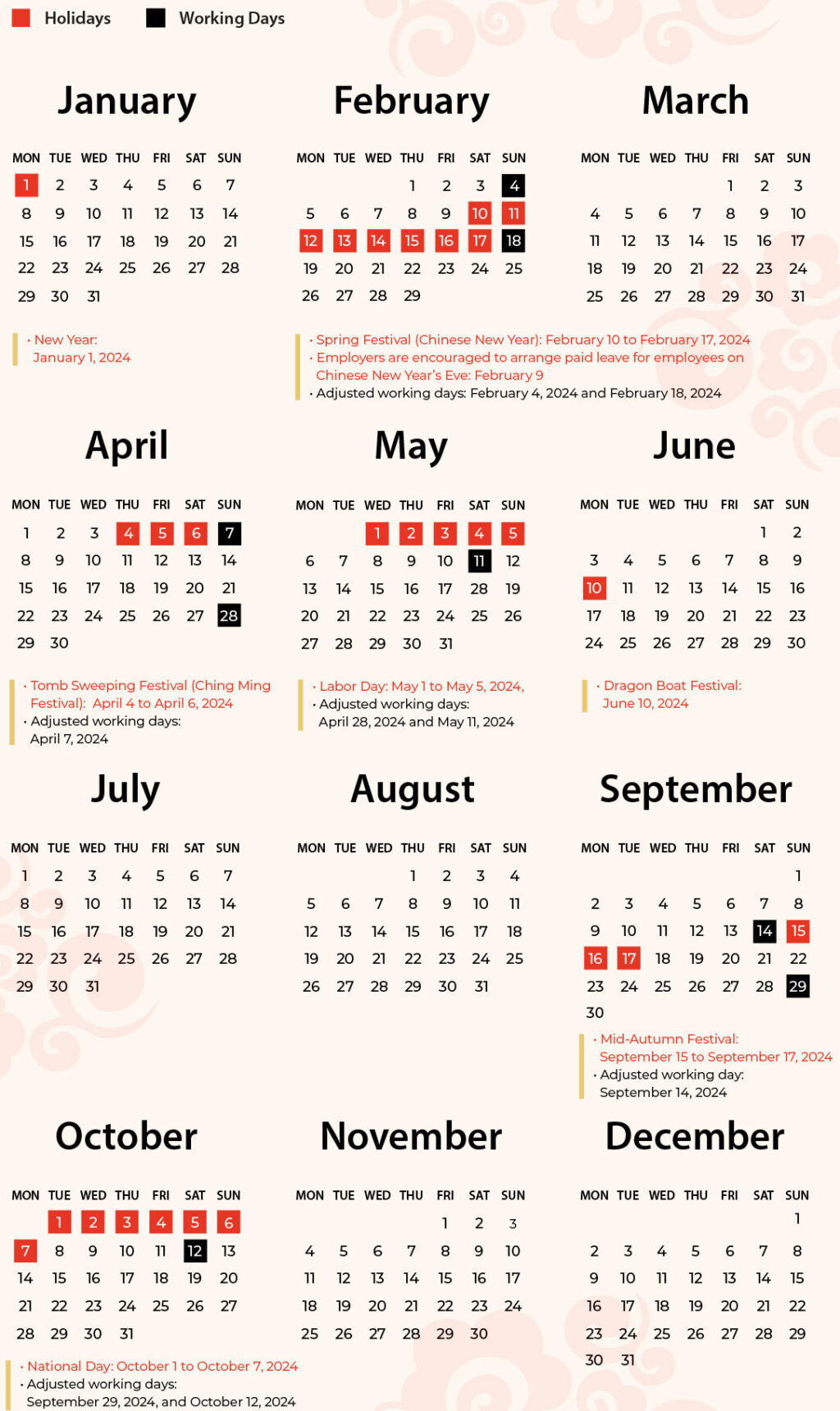
Official China Public Holiday 2024 schedule
New Year
- January 1, 2024 (one rest day)
Spring Festival (Chinese New Year)
- February 10 to February 17, 2024 (eight rest days in total)
- Employers are encouraged to arrange paid leave for employees on Chinese New Year’s Eve (February 9)
- Adjusted working days: February 4, 2024 (Sunday) and February 18, 2024 (Sunday)
Tomb Sweeping Festival (Ching Ming Festival)
- April 4 to April 6, 2024 (three rest days in total, in connection with one weekend day)
- Adjusted working days: April 7, 2024 (Sunday)
Labor Day
- May 1 to May 5, 2024 (five rest days in total)
- Adjusted working days: April 28, 2024 (Sunday) and May 11, 2024 (Saturday)
Dragon Boat Festival
- June 10, 2024 (three rest days in total, in connection with the weekend)
Mid-Autumn Festival
- September 15 to September 17, 2024 (three rest days in total)
- Adjusted working days: September 14, 2024 (Saturday)
National Day
- October 1 to October 7, 2024 (seven rest days in total)
- Adjusted working days: September 29, 2024 (Sunday) and October 12, 2024 (Saturday)
Bisq: Empowering You in the World of Cryptocurrency Trading

In the ever-evolving realm of cryptocurrency trading, security, privacy, and transparency have become paramount. Bisq, the decentralized exchange platform hosted at bisq.network, stands as a beacon of innovation, offering users a truly peer-to-peer experience in the world of digital currencies.
How Bisq Works
At its core, Bisq operates as a decentralized exchange network, allowing users to buy and sell cryptocurrencies directly with one another. Unlike traditional exchanges, Bisq cuts out the middleman, empowering users with direct control over their transactions. This open-source platform facilitates secure trades, ensuring that your funds and personal data remain in your hands.
Advantages of Decentralization
Decentralization, the cornerstone of Bisq, offers a myriad of advantages over centralized platforms. First and foremost, decentralization eliminates the need for intermediaries, reducing the risk of hacks and ensuring that you retain ownership of your assets throughout the trading process. Additionally, decentralized exchanges are not bound by geographical restrictions, providing a truly global marketplace for cryptocurrency enthusiasts.
Bisq’s Focus on Privacy
Privacy is not just a feature at Bisq; it’s a fundamental right. Bisq employs innovative techniques like Tor and end-to-end encryption to protect your identity and transaction data. With Bisq, you can trade confidently, knowing that your personal information is shielded from prying eyes. The platform never holds your funds, further enhancing the security of your assets. Never forget: Not your keys, not your Bitcoin!
In a world where data breaches and privacy concerns abound, Bisq stands as a testament to the power of decentralized, peer-to-peer trading. By leveraging cutting-edge technology and a commitment to user empowerment, Bisq provides a safe, private, and transparent environment for cryptocurrency enthusiasts.
Embrace the future of trading with Bisq – where your security, privacy, and control are never compromised. Join the decentralized revolution and experience cryptocurrency trading like never before.
Take charge. Trade freely. Trust Bisq.
Money, wealth, fortune – how much is enough?


To #Bitcoin investors and enthusiasts panting after the “Lambo”, I recommend reading Andreas Eschenbach’s “One Trillion Dollars”.
$1,000,000,000,000 – a thousand billion!
What would you do with a trillion US Dollars?
Written in pre-Bitcoin era, it takes a sideways look at fiat money, corporations, global economy, mututal dependencies, predation, globalization, banks, governments, and reveals indirect connections that are rarely clear in the first – even after a longer look.
Can wealth pursue an ideology? For the good of all? Do interests make sense? Does wealth equal power? Does responsibility result from it?
Where would it begin and where would the limits of that responsibility be?
#Bitcoin fixes this.
or
#Bitcoin can fix this. 🤔


Den #Bitcoin Investoren und Enthusiasten, die dem „Lambo“ hinterher hecheln, empfehle ich Andreas Eschenbachs “Ein Billion Dollar” zu lesen.
1.000.000.000.000 $ – Tausend Milliarden!
Was würdest Du mit einer Billion US Dollar tun?
Geschrieben in der Prä-Bitcoin-Ära wirft es einen Seitenblick auf Fiatgeld, Konzerne, Abhängigkeiten, Raubbau, Globalisierung, Banken, Regierungen und enthüllt indirekte Zusammenhänge, die im Alltag selten — auch nach einem längeren Blick — klar sind.
Kann Reichtum eine Ideologie verfolgen? Zum Wohl aller? Machen Zinsen Sinn? Ist Reichtum gleich Macht? Resultiert daraus Verantwortung?
Wo begönne sie und wo wären Grenzen dieser Verantwortung?
#Bitcoin fixes this.
or
#Bitcoin can fix this. 🤔
I operate my own little Lightning Node
Feel free to open a channel e.g. with
clightning
lightning-cli connect 0366217f4a7abf70842f794e94a4cbddc249d5cbaf9c0ffd0b7e4638d9bf07845d 81.7.17.202 9735
lnd
lncli connect 0366217f4a7abf70842f794e94a4cbddc249d5cbaf9c0ffd0b7e4638d9bf07845d@81.7.17.202:9735
eclair
eclair-cli connect 0366217f4a7abf70842f794e94a4cbddc249d5cbaf9c0ffd0b7e4638d9bf07845d@81.7.17.202:9735
(please be note that you have to remove hyphens from the line above, after copy/paste somewhere) or try my already working online tipping tool. Check it out! Send me some Satoshis throught the Lightning ⚡️ Network (beta, but fast as lightning!)
Multi-Signature: Unlocking Enhanced Security and Trust in the Bitcoin World
In the ever-evolving world of cryptocurrencies, security is paramount. One innovative solution that has gained significant traction is the use of multi-signature (multisig) wallets. These wallets require multiple keys to authorize a transaction, adding an extra layer of protection against theft and fraud. In this blog post, we will briefly explore the fascinating concept of multisig wallets, delve into their advantages, and highlight some compelling use cases that showcase their versatility.
What are Multi-Signature Wallets?
Imagine a secure locker with two locks, each requiring a different key held by separate parties. Multi-signature wallets operate on a similar principle. They demand the authorization of transactions through multiple keys, ensuring that a group of users must sign to approve a transaction. In the world of cryptocurrencies, multisig wallets require at least two private keys to sign a transaction, making them considerably more secure than traditional single-signature wallets.
Advantages of Multi-Signature Wallets:
- Enhanced Security: With multisig wallets, the risk of unauthorized access or theft is significantly reduced. Even if one key is compromised, the funds remain secure as additional signatures are required to initiate any transaction.
- Distributed Responsibility: Multisig wallets enable the division of possession and responsibility among multiple individuals or entities. This decentralized approach eliminates the vulnerability of a single point of failure, making it exceedingly difficult for malicious actors to compromise the wallet.
- Trustless Environments: Multisig wallets are an ideal solution for groups or organizations that need to administer funds in trustless environments. By requiring multiple signatures from parties who may not know each other personally, it ensures a high level of accountability and prevents unilateral control over the assets.
Use Cases of Multi-Signature Wallets:
- Joint Accounts: Multisig wallets are perfect for joint accounts, such as those held by couples or business partners. For example, a 2-of-2 multisig wallet would require both spouses’ signatures to spend the funds, ensuring mutual consent.
- Trustworthy Escrow: In buyer-seller transactions with trustless escrow, multisig wallets provide a secure mechanism. A 2-of-3 wallet involving the buyer, seller, and a trusted third-party arbitrator ensures fair and reliable transaction settlements.
- Organizational Funds: Multisig wallets offer an ideal solution for organizations and boards that require collective decision-making. For instance, a 2-of-3 multisig wallet can be used, where any two out of three directors must agree to spend the funds, ensuring transparency and reducing the risk of misuse.
- Two-Factor Authentication: Multisig wallets can serve as an extra layer of security for two-factor authentication. Requiring private keys from both a primary computer and a smartphone ensures that an attacker must compromise both devices to access the funds.
- Decentralized Cold Storage: To safeguard funds in cold storage, multisig wallets provide an excellent solution. By distributing keys across multiple physical locations, such as homes, banks, and offices, the risk of loss due to theft or destruction of a single location is mitigated.
Conclusion
In the dynamic landscape of cryptocurrencies, multi-signature wallets have emerged as a powerful tool for bolstering security and trust. By requiring multiple signatures to authorize transactions, these wallets provide enhanced protection against theft and fraud. From joint accounts to organizational funds, the applications of multisig wallets are diverse and far-reaching. As the cryptocurrency ecosystem continues to evolve, the adoption of multisig wallets is likely to increase, offering users a robust and reliable means to safeguard their digital assets.
I operate my own little Lightning Node
Feel free to open a channel e.g. with
clightning
lightning-cli connect 0366217f4a7abf70842f794e94a4cbddc249d5cbaf9c0ffd0b7e4638d9bf07845d 81.7.17.202 9735
lnd
lncli connect 0366217f4a7abf70842f794e94a4cbddc249d5cbaf9c0ffd0b7e4638d9bf07845d@81.7.17.202:9735
eclair
eclair-cli connect 0366217f4a7abf70842f794e94a4cbddc249d5cbaf9c0ffd0b7e4638d9bf07845d@81.7.17.202:9735
(please be note that you have to remove hyphens from the line above, after copy/paste somewhere) or try my already working online tipping tool. Check it out! Send me some Satoshis throught the Lightning ⚡️ Network (beta, but fast as lightning!)
What is that about the different types of Bitcoin addresses?
Are you new to Bitcoin and wondering about the different types of Bitcoin addresses?
Bitcoin addresses are important because they contain information about who can access the Bitcoin that has been sent to them. In this post, we will take a closer look at the four different types of Bitcoin addresses, their unique features, and how they work.
Legacy Addresses (P2PKH)
Legacy addresses are the original Bitcoin addresses and start with the number 1. These addresses are simply the hash of the public key to your private key. Legacy addresses are the most expensive address type as they use the most amount of space inside a transaction. However, if you have an old wallet that is incompatible with newer address types, you may still need to use a legacy address.
Pay to Script Hash (P2SH)
Pay-to-Script-Hash addresses start with the number 3. These addresses are not the hash of the public key, but of a script that involves certain spending conditions, which stay hidden from the sender. P2SH addresses can even make use of SegWit and save transaction fees. Sending to a P2SH address is roughly 26% cheaper than using a wallet with legacy addresses.
Native SegWit (P2WPKH)
Native SegWit addresses start with bc1q. This type of address reduces the amount of information stored in the transaction even more by not keeping the signature and script within the transaction, but in the witness. Using this type, you can save an additional 16% over the P2SH addresses, adding up to over 38% savings over legacy addresses. This is currently the most used standard for addresses.
Taproot (P2TR)
Taproot addresses start with bc1p. Taproot addresses are not used yet, but the Bitcoin network will perform the taproot soft-fork in November 2021. This will enable a lot of new smart-contract capabilities for Bitcoin addresses and improve the privacy of spending such transactions.
To identify the type of a Bitcoin address, you can look at the first letters of it. If it starts with “1”, it’s a legacy address. If it starts with “3”, it’s a P2SH address. If it starts with “bc1q”, it’s a native SegWit and if the first 4 letters are “bc1p”, it’s a taproot address.
You can generate a Bitcoin address by clicking on “Receive” within your Bitcoin wallet. You can create as many different Bitcoin addresses as you want. For privacy reasons, it is advised to not re-use an address.
Most Bitcoin wallets default to bech32 (native SegWit) addresses, which saves the highest amount of transaction costs. If your wallet lets you choose which type you want to use, you should use native SegWit addresses.
Q&A:
- What’s in a Bitcoin address? The first letters of a Bitcoin address hold clues about the type of address it is. Whether it’s a legacy address that starts with “1”, a P2SH address that begins with “3”, a native segwit address that starts with “bc1q”, or a taproot address that starts with “bc1p”, each type serves a unique purpose.
- Where to find a Bitcoin address? If you need a Bitcoin address, look no further than your own wallet. By clicking on “Receive,” you can generate as many addresses as you need. However, for privacy’s sake, it’s best not to reuse the same address.
- Is changing your Bitcoin address necessary? No, it’s not necessary to change your Bitcoin address unless you’re sending funds to a new address. In that case, you’ll have to create a new address in your wallet and conduct a regular transaction to the new address.
- Which Bitcoin address should you use? If you have a choice, opt for a native segwit address. Most wallets default to bech32 addresses, which saves you money in transaction costs.
- How do Bitcoin addresses enable transactions? Bitcoin addresses are key to enabling transactions. By proving that you own the private key to a given address, you’re able to initiate a transaction from it. Without that proof of ownership, no valid transaction can take place.
- Are Bitcoin addresses case-sensitive? No, Bitcoin addresses aren’t case-sensitive.
I operate my own little Lightning Node
Feel free to open a channel e.g. with
clightning
lightning-cli connect 0366217f4a7abf70842f794e94a4cbddc249d5cbaf9c0ffd0b7e4638d9bf07845d 81.7.17.202 9735
lnd
lncli connect 0366217f4a7abf70842f794e94a4cbddc249d5cbaf9c0ffd0b7e4638d9bf07845d@81.7.17.202:9735
eclair
eclair-cli connect 0366217f4a7abf70842f794e94a4cbddc249d5cbaf9c0ffd0b7e4638d9bf07845d@81.7.17.202:9735
(please be note that you have to remove hyphens from the line above, after copy/paste somewhere) or try my already working online tipping tool. Check it out! Send me some Satoshis throught the Lightning ⚡️ Network (beta, but fast as lightning!)



